本文最后更新于:2025年6月25日 上午
Lab Environment 下载docker文件、解压、运行docker
1 2 3 4 5 6 7 $ curl https://seedsecuritylabs.org/Labs_20.04/Files/Crypto_PKI/Labsetup.zip --output pki.zip $ unzip pki.zip $ dcbuild $ dcup
这里docker可能没有速度,把/etc/docker/daemon.json文件写入下面的源即可
1 2 3 4 5 6 7 8 # cat /etc/ docker/daemon.json"registry-mirrors" : ["https://hub-mirror.c.163.com" ,"https://mirror.baidubce.com"
SEED VM已经提前做好了命令替换 ,可以看到.bashrc有如下代码
1 2 3 4 5 6 # Commands for for docker
给/etc/hosts文件增加映射
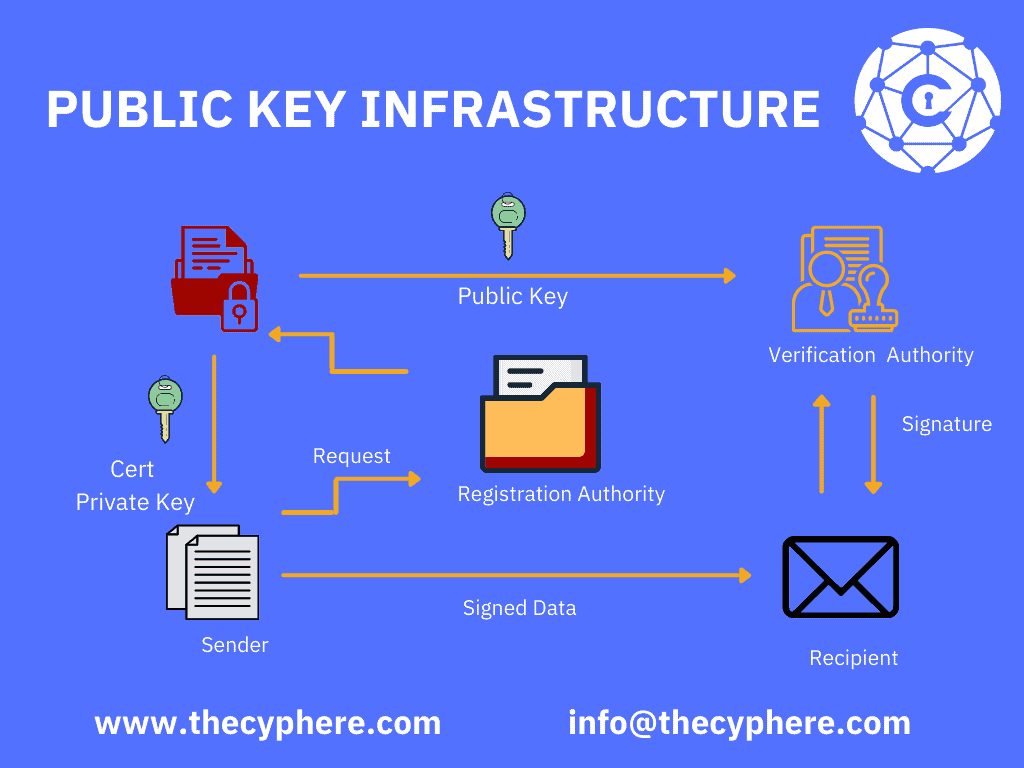
Task 1: Becoming a Certificate Authority (CA)
证书颁发机构(CA)是颁发数字证书的可信实体。数字证书证明证书的指定主体对公钥的所有权。许多商业 CA 被视为根 CA; VeriSign 是编写本文时最大的 CA。希望获得商业 CA 颁发的数字证书的用户需要向这些 CA 支付费用。
在这个实验室,我们需要创建数字证书。我们自己将成为一个根 CA,并为这个 CA 生成一个证书。然后使用这个 CA 为其他 CA (例如服务器)颁发证书。
与通常由另一个 CA 签名的其他证书不同,根 CA 的证书是自签名的。Root CA 的证书通常预先加载到大多数操作系统、 Web 浏览器和其他依赖 PKI 的软件中。根 CA 的证书是无条件受信任的
配置文件 openssl.conf
为了使用 OpenSSL 创建证书,必须有一个配置文件。
配置文件通常有一个扩展名.Cnf。它由三个 OpenSSL 命令使用: ca、 req 和 x509
默认情况下,OpenSSL 使用来自/usr/lib/ssl/OpenSSL.cnf 的配置文件。因为我们需要对这个文件进行更改,所以我们将把它复制到我们的工作目录中,并指示 OpenSSL 使用这个副本。配置文件的[ CA default ]部分显示了我们需要准备的默认设置。
在使用 OpenSSL 生成证书时,可以使用 -config 参数来指定要使用的 openssl.cnf 配置文件。该参数允许你提供自定义的配置文件路径。
以下是使用 OpenSSL 命令生成证书时指定 openssl.cnf 文件的示例命令:
1 openssl req -new -config /path/to/openssl.cnf -keyout private.key -out csr.csr
进入/usr/lib/ssl看一下
1 2 3 4 5 6 [06/21/23]seed@VM:.../ssl$ ll
查看一下openssl.cnf文件的内容,很长,我们关注一下配置文件的[ CA default ]部分,它显示了我们需要准备的默认设置
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 ####################################################################'no' to allow creation of with same subject."traditional" with caution.
设置
值
解释
dir
./demoCA
所有文件存放的根目录
certs
$dir/certs
存储已颁发证书的目录
crl_dir
$dir/crl
存储已颁发CRL的目录
database
$dir/index.txt
数据库索引文件
unique_subject
no
是否允许创建具有相同主题的多个证书
new_certs_dir
$dir/newcerts
存储新创建证书的默认目录
certificate
$dir/cacert.pem
CA证书文件
serial
$dir/serial
当前序列号文件
crlnumber
$dir/crlnumber
当前CRL号码文件
crl
$dir/crl.pem
当前CRL文件
private_key
$dir/private/cakey.pem
私钥文件
x509_extensions
usr_cert
添加到证书的扩展
name_opt
ca_default
主题名称选项
cert_opt
ca_default
证书字段选项
copy_extensions
copy
复制扩展选项(当前被注释掉)
在家目录下创建工作目录CA,将openssl.cnf复制到此处,删除文件中copy_extensions = copy和unique_subject = no的注释
将该文件复制到工作目录之后,需要按照配置文件中指定的方式创建几个子目录。我们需要创建几个子目录mkdir certs crl newcerts
对于 index.txt 文件,只需创建一个空文件。对于serial文件,在文件中放置一个字符串格式的数字(例如1000)。一旦设置了配置文件 openssl.cnf,就可以创建和颁发证书。
创建几个必须的文件
1 2 3 4 5 6 7 8 9 10 [06/21 /23 ]seed@VM :~/demoCA $ mkdir certs crl newcerts21 /23 ]seed@VM :~/demoCA $ ls21 /23 ]seed@VM :~/demoCA $ echo 1000 > serial21 /23 ]seed@VM :~/demoCA $ echo '' > index.txt21 /23 ]seed@VM :~/demoCA $ ls21 /23 ]seed@VM :~/demoCA $ ls
如前所述,我们需要为 CA 生成一个自签名证书。这意味着这个 CA 是完全可信的,它的证书将充当根证书。可以运行以下命令为 CA 生成自签名证书:
在命令行中指定主题信息和密码,这样就不会提示您输入任何其他信息。在下面的命令中,我们使用-subj 来设置主题信息,使用-passout pass: dees 来设置 dees 的密码。
1 2 3 4 5 openssl req -x509 -newkey rsa:4096 -sha256 -days 3650 \ca .key -out ca .crt \"/CN=www.modelCA.com/O=Model CA LTD./C=US" \s:dees \cnf
执行该命令后,将生成一个名为 ca.key 的私钥文件和一个名为 ca.crt 的自签名根证书文件,可以将该根证书用于签发其他证书
-x509:指定生成自签名的证书,而无需先生成证书请求(CSR)-newkey rsa:4096:生成一个新的 RSA 4096 位的密钥对。-sha256:使用 SHA-256 算法进行证书哈希。-days 3650:证书的有效期为 3650 天(约为 10 年)。-keyout ca.key:将生成的私钥保存到 ca.key 文件。-out ca.crt:将生成的证书保存到 ca.crt 文件。-subj "/CN=www.modelCA.com/O=Model CA LTD./C=US":指定证书的主题信息,包括通用名称(Common Name)、组织(Organization)和国家代码(Country Code)。-passout pass:dees:指定私钥的密码为 “dees”。/path/to/your/openssl.cnf 配置文件的路径
1 2 3 4 5 6 7 8 9 10 11 12 13 [06/22/23]seed@VM:~/demoCA$ openssl req -x509 -newkey rsa:4096 -sha256 -days 3650 \> -keyout ca.key -out ca.crt \ > -subj "/CN=www.modelCA.com/O=Model CA LTD./C=US" \ > -passout pass:dees \ > -config > -config ./tmp_openssl.cnf
我们可以使用以下命令查看 X509证书的解码内容和 RSA 密钥(- text 意味着将内容解码为纯文本;-noout 意味着不打印编码版本)
1 2 openssl x509 -in ca.crt -text -nooutkey -text -noout
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 [06/21/23]seed@VM:~/.../demoCA$ openssl x509 -in ca.crt -text -noout
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 [06/21/23]seed@VM:~/.../demoCA$ openssl rsa -in ca.key -text -noout
Q: What part of the certificate indicates this is a CA’s certificate?
在证书中,判断是否为CA证书可以查看”Basic Constraints”扩展字段。在这个证书中,存在并标记为关键的”X509v3 Basic Constraints”扩展字段。其取值为”CA:TRUE”,表示这是一张CA证书。该扩展字段用于识别证书是否具有签发其他证书的权限。
What part of the certificate indicates this is a self-signed certificate?
要判断证书是否为自签名证书,可以比较主题字段和颁发者字段。在这个证书中,主题和颁发者字段相同:”CN = www.modelCA.com , O = Model CA LTD., C = US”。当主题和颁发者字段相同的时候,表明证书是自签名的。
In the RSA algorithm, we have a public exponent e, a private exponent d , a modulus n , and two secret numbers p and q , such that n = p * q . Please identify the values for these elements in your certificate and key files.
modulus:模数,由两个素数相乘得到
publicExponent:公开指数,表示用于加密的公钥指数,这里是65537。
privateExponent:私有指数,表示用于解密的私钥指数。
prime1和prime2:两个素数,用于生成模数。
Task 2: Generating a Certificate Request for Your Web Server 一个名为bank32.com(请将其替换为您自己的Web服务器名称)的公司希望从我们的CA获取公钥证书。首先,它需要生成一个证书签名请求(CSR),其中包括公司的公钥和身份信息。CSR将被发送给CA,CA将验证请求中的身份信息,然后生成一个证书。 生成CSR的命令与我们用于创建CA的自签名证书的命令非常相似,唯一的区别是使用了”-x509”选项。没有该选项,该命令将生成一个请求;而使用该选项,该命令将生成一个自签名证书。
1 2 3 4 openssl req -newkey rsa:2048 -sha256 \keyout server.key -out server.csr \ subj "/CN=www.gls23.com/O=gls23 Inc./C=US" \ passout pass: dees
req:指定使用 OpenSSL 的 req 命令。-newkey rsa:2048:生成一个新的 RSA 密钥对,密钥长度为 2048 位。-sha256:使用 SHA-256 算法进行摘要计算。-keyout server.key:将生成的私钥保存到名为 server.key 的文件中。-out server.csr:将生成的 CSR 保存到名为 server.csr 的文件中。-subj "/CN=www.chenyang2022.com/O=Chenyang2022 Inc./C=US":设置 CSR 的主题信息,包括常用名称 (Common Name)、组织名称 (Organization) 和国家/地区 (Country)。-passout pass:dees:设置私钥文件的加密密码为 “dees”。
Adding Alternative names 浏览器实施的主机名匹配策略要求证书中的通用名称必须与服务器的主机名匹配,否则浏览器将拒绝与服务器通信。为了允许一个证书具有多个名称,X.509 规范定义了附加到证书上的扩展。这个扩展称为主体备用名称(Subject Alternative Name,SAN)。使用 SAN 扩展,可以在证书的 subjectAltName 字段中指定多个主机名。为了生成带有这样一个字段的证书签名请求,我们可以将所有必要的信息放在一个配置文件中或者通过命令行提供。在这个任务中,我们将使用命令行方法(配置文件方法在另一个 SEED 实验室,即 TLS 实验室中使用)。我们可以向 “openssl req” 命令添加以下选项。需要注意的是,subjectAltName 扩展字段还必须包括来自通用名称字段的内容;否则,通用名称将不被接受为有效名称。
1 2 3 4 5 6 openssl req -newkey rsa:2048 -sha256 \"/CN=www.gls23.com/O=gls23 Inc./C=US" \s:dees \com
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 [06/21/23] seed@VM :~/demoCA$ openssl req -newkey rsa :2048 -sha256 \"/CN=www.gls23.com/O=Bank32 Inc./C=US" \pass :dees \"subjectAltName = DNS:www.gls2023.com, \ > DNS:www.gls2024.com" 'server.key' 06 /21 /23 ]seed@VM :~/demoCA$ openssl req -in server.csr -text -nooutRequest :Data :Version : 1 (0 x0)Subject : CN = www.gls23.com, O = Bank32 Inc., C = USInfo :Algorithm : rsaEncryptionPublic-Key : (2048 bit)Modulus :00 :a4:10 :d3:4 d :cf :98 :01 :14 :4 e :5 f :6 c :c1:2 b :ba :9 e :64 :cb :6 c :3 a :e2:35 :27 :0 c :03 :c5:c4:f0:2 b :53 :5 b :11 :40 :e6:ab :df :e1:56 :d5:a7:4 c :56 :25 :a8:7 c :5 c :79 :6 b :e7:16 :31 :98 :a9:96 :26 :e0:e2:c5:93 :ec :d9:b8:cc :53 :46 :e7:13 :79 :27 :cd :be :33 :b0:d1:8 e :b6:59 :91 :5 d :48 :d8:a8:66 :57 :0 a :2 d :a1:be :82 :61 :bb :b5:c4:4 f :7 e :78 :d5:6 b :56 :51 :43 :78 :95 :83 :02 :54 :91 :7 a :0 e :66 :fd :9 b :d4:26 :fe :97 :46 :e7:57 :03 :10 :4 a :0 b :45 :bd :b7:96 :23 :8 f :be :14 :57 :84 :52 :4 c :4 a :06 :0 f :55 :9 b :19 :52 :30 :1 a :26 :b2:fe :00 :45 :e0:02 :0 b :a5:0 d :7 a :80 :df :73 :55 :65 :84 :28 :63 :93 :d1:00 :80 :5 e :52 :7 c :b5:24 :1 b :e9:a0:7 f :20 :43 :55 :e2:8 d :5 e :03 :02 :82 :aa :72 :54 :97 :83 :cb :5 e :8 b :b5:f9:b8:41 :11 :d7:b9:9 c :fd :5 c :9 b :51 :6 d :73 :18 :e4:48 :4 f :c1:54 :4 a :7 d :d0:a0:e7:dc :1 a :57 :fd :4 c :7 d :48 :2 d :b2:0 a :74 :bc :68 :3 a :8 b :3 b :97 :ec :bf :12 :af :36 :63 :50 :9 f :4 b :6 e :e8:31 :02 :d8:e5:d1:e5:2 f :edExponent : 65537 (0 x10001)Attributes :Extensions :Name : DNS :www.gls2023.com, DNS :www.gls2024.comAlgorithm : sha256WithRSAEncryption4 c :f5:d9:b2:f7:4 c :8 d :19 :f1:57 :7 e :6 c :57 :3 d :d6:a9:89 :ad :cb :cb :37 :c5:44 :00 :c2:31 :cc :64 :a8:2 b :51 :ca :9 d :9 b :04 :d0:07 :c9:c8:f6:fc :56 :ba :0 c :c7:b2:bb :aa :3 c :98 :15 :e8:3 f :8 f :4 d :bc :4 e :d5:32 :41 :69 :d5:83 :6 f :8 c :68 :bd :c1:22 :35 :9 a :fa :3 a :71 :22 :c1:71 :5 a :39 :5 d :0 b :13 :4 c :d4:bb :d5:b4:d2:eb :be :e7:53 :c4:50 :da :77 :00 :23 :14 :86 :a6:98 :cd :80 :9 d :4 b :b7:51 :1 b :f1:81 :48 :e5:1 c :3 c :dc :f2:5 a :b7:a4:43 :a3:5 b :ad :bf :7 f :66 :59 :cc :12 :ca :23 :c0:a1:da :38 :ff :c1:e8:78 :cd :b5:5 f :43 :e8:82 :4 f :d3:76 :a9:3 e :e2:54 :ad :85 :66 :18 :da :19 :bd :c4:5 b :f7:f2:53 :13 :ea :44 :73 :be :bb :8 a :cb :7 c :20 :18 :b2:65 :96 :24 :22 :43 :ab :5 f :11 :62 :18 :4 f :7 f :3 a :b6:47 :e1:f2:70 :9 d :95 :3 c :eb :aa :d5:0 a :5 c :d9:0 d :83 :7 f :d0:bd :ae :b4:76 :a3:a8:a6:7 f :94 :0 f :4 f :8 a :41 :7 e :e7:fe :9 c :bc :ee :06 :67 :10 :60 :57 :58 :78 :c7:65 :f3:5 e :52 :1 c :02 :5 e :f8:98 :9 c :05 :58 :73 :b0:c0:56 :82 :52 :34
Task 3: Generating a Certificate for your server CSR 文件需要有 CA 的签名才能形成证书。在现实世界中,CSR 文件通常被发送到受信任的 CA 以获得签名。在这个lab中,我们将使用我们自己的可信 CA 来生成证书。下面的命令使用 CA 的 CA.crt 和 CA.key 将证书签名请求(server.csr)转换为 X509证书(server.crt) :
注意我的配置文件在./my_openssl.cnf
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 [06/22/23]seed@VM:~/CA$ openssl ca -config ./my_openssl.cnf -policy policy_anything \> -md sha256 -days 3650 \ > -in server.csr -out server.crt -batch \ > -cert ./ca.crt -keyfile ./ca.key
执行之后,文件出现了变化
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 [06/22/23]seed@VM:~/CA$ tree .
查看一下server.crt
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 [06/22/23] seed@VM :~/CA$ openssl x509 -in server.crt -text -nooutCertificate :Data :Version : 3 (0 x2)Number : 4097 (0 x1001)Algorithm : sha256WithRSAEncryptionIssuer : CN = www.modelCA.com, O = Model CA LTD., C = USNot Before : Jun 22 14 :54 :43 2023 GMTNot After : Jun 19 14 :54 :43 2033 GMTSubject : C = US, O = gls23 Inc., CN = www.gls23.comInfo :Algorithm : rsaEncryptionPublic-Key : (2048 bit)Modulus :00 :95 :72 :09 :22 :45 :48 :33 :58 :7 a :a3:9 b :27 :d5:d8:3 d :5 f :87 :86 :7 a :10 :d7:40 :a2:94 :6 c :c6:0 e :84 :ff :e4:61 :10 :9 c :fe :f4:a9:90 :09 :c1:a1:d3:7 a :59 :10 :9 a :2 e :eb :e2:29 :9 c :04 :cc :48 :17 :e4:1 b :06 :28 :d7:d3:f5:88 :0 c :08 :ea :c8:ad :6 d :e5:eb :20 :9 d :2 b :33 :bc :ce :36 :7 a :c8:7 c :21 :10 :97 :2 e :27 :ea :24 :5 b :5 b :07 :f6:d9:90 :1 d :8 f :bf :b6:00 :3 a :c9:0 e :37 :58 :ca :0 c :30 :18 :b3:20 :0 f :45 :01 :99 :78 :ce :81 :b8:56 :93 :29 :58 :3 c :ea :e9:7 d :a7:cf :d9:f4:dc :37 :58 :75 :34 :a6:a5:9 b :a5:1 f :64 :a0:70 :ca :b7:24 :1 a :50 :f9:6 f :64 :3 a :30 :80 :89 :a1:dc :fc :72 :ce :24 :49 :eb :c8:b6:5 d :b4:e5:bd :f5:45 :8 d :c4:a7:c3:e8:28 :c2:b4:e3:7 e :8 a :48 :75 :b3:81 :ab :bc :0 f :6 d :43 :3 c :d8:9 e :15 :17 :ee :5 c :61 :1 d :e7:76 :27 :31 :38 :66 :47 :68 :85 :e7:b2:80 :fd :e1:98 :36 :70 :12 :8 e :ad :85 :00 :fc :45 :1 b :fe :72 :6 b :e9:2 e :3 f :e6:6 f :b1:45 :95 :af :6 c :21 :14 :1 b :64 :3 a :f8:87 :34 :28 :b1:91 :2 a :2 f :3 dExponent : 65537 (0 x10001)extensions :Constraints : CA :FALSEComment : Identifier : 53 :6 B :EA :44 :75 :F5:0 D :AE :C1:B7:01 :67 :E5:E5:0 C :EF :42 :0 E :9 F :57 Identifier : keyid :85 :43 :B9:78 :0 E :00 :2 C :30 :DB :49 :AC :E4:00 :03 :EF :B3:E0:D8:AD :49 Name : DNS :www.gls2023.com, DNS :www.gls2024.comAlgorithm : sha256WithRSAEncryption62 :b0:a6:8 a :15 :35 :b4:8 f :5 f :1 a :18 :89 :d2:32 :6 e :10 :6 f :19 :85 :39 :c1:ca :49 :0 e :d4:f0:a6:85 :b9:ac :0 b :7 a :8 c :11 :19 :66 :7 f :9 d :af :1 d :1 c :86 :60 :e6:f5:ac :70 :5 a :ba :f7:1 e :e1:65 :21 :31 :4 d :fe :33 :74 :64 :16 :66 :9 a :2 b :02 :74 :cf :e3:93 :af :1 f :86 :05 :db :84 :34 :7 f :73 :69 :3 c :d1:be :f3:f5:0 f :8 e :e8:98 :bf :5 b :5 c :55 :73 :33 :09 :0 a :2 a :41 :db :58 :d3:59 :e1:2 b :e3:92 :96 :d4:1 d :d3:b3:39 :27 :50 :8 f :06 :4 b :0 c :68 :97 :9 f :a0:fe :05 :1 a :0 f :95 :95 :24 :3 d :4 f :70 :f2:69 :6 a :0 e :eb :b8:00 :a3:dc :29 :43 :28 :51 :df :f5:8 d :e6:89 :79 :2 c :ef :50 :22 :b1:9 e :17 :09 :76 :75 :30 :32 :10 :f0:73 :34 :22 :26 :13 :64 :47 :3 b :39 :ac :c1:3 f :34 :ff :61 :e8:f6:02 :bf :15 :17 :33 :30 :95 :e2:71 :14 :f1:c8:be :42 :b4:83 :eb :de :52 :ce :d4:c2:4 e :ed :bb :cf :91 :3 f :09 :30 :ce :68 :50 :39 :4 a :37 :81 :c6:fb :32 :ca :fb :2 e :ef :78 :06 :8 a :d7:a1:69 :a8:1 f :6 b :e3:14 :59 :df :95 :99 :fc :a5:12 :0 d :54 :d4:03 :d6:cf :1 f :a0:e1:1 d :ae :66 :cd :03 :db :78 :65 :60 :f7:55 :c9:79 :19 :fd :d2:db :45 :b6:c2:68 :f0:04 :80 :65 :f7:40 :87 :c3:dc :6 e :18 :9 f :82 :7 d :db :16 :e9:02 :c9:58 :7 b :b5:ed :62 :6 a :d9:2 f :3 a :ca :35 :2 d :3 e :ae :9 f :be :e6:dd :fb :a9:ac :10 :db :41 :4 a :e0:e8:6 a :32 :2 b :44 :8 a :3 e :a5:7 c :c4:88 :6 c :ce :ef :93 :48 :de :27 :21 :fe :df :a7:19 :f2:01 :b7:d3:7 e :5 a :24 :fd :15 :3 e :7 e :07 :46 :05 :b4:4 c :b8:84 :25 :28 :bc :55 :e6:8 d :17 :33 :f4:3 d :36 :84 :5 b :fe :56 :61 :54 :7 c :da :47 :b9:57 :bd :0 f :b9:d8:86 :82 :65 :70 :95 :6 e :38 :5 b :98 :17 :c6:01 :ac :a0:4 a :01 :5 d :a8:82 :92 :ca :38 :00 :54 :3 e :38 :1 e :1 d :3 e :17 :40 :c5:59 :7 e :ff :39 :04 :2 f :99 :bb :66 :07 :39 :bb :14 :a8:e6:09 :09 :ea :54 :e7:3 e :18 :3 a :5 d :72 :44 :b0:5 b :48 :92 :69 :81 :05 :ec :94 :fb :6 f :56 :4 e :5 f :88 :4 f :fe :5 f :ac :55 :33 :3 e :e1:27 :e0:c2:66 :5 c :70 :ea :b6:d1:0 e :71 :7 b :92 :f7:3 d :8 b :a4:1 b :38 :84 :d3:c9:ec :db :f1:63 :89 :5 a :5 a :6 e :0 c :27 :08 :d3:16 :4 a :59
Task 4: Deploying Certificate in an Apache-Based HTTPS Website 编辑我们自己网站的apache ssl.conf文件
1 2 3 4 5 6 7 8 9 10 11 12 13 $ cat apache_ssl.conf 443 > .gls23 .com .gls2023 .com .gls2024 .com .html .crt .key [06/22/23] seed@VM:~/.../image_www$
可以看到第九行、第十行需要文件。因此把server.crt和server.key复制到容器的certs文件夹
编辑一下容器的Dockerfile,如下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 FROM dockerproxy.com/handsonsecurity/ seed-server:apache-php/var/ www/gls23COPY ./index.html ./i ndex_red.html $WWWDIR/COPY ./apache_ssl.conf / etc/apache2/ sites-availableCOPY ./certs/ server.crt ./certs/ server.key /certs/ 400 /certs/ server.key \644 $WWWDIR/index.html \644 $WWWDIR/index_red.html \/dev/ null
下面构建容器镜像、运行容器、进入容器内部、启动Apache服务
1 2 3 4 5 6 7 8 9 10 11 $ dcbuild$ dcup$ docker image ls $ docker ps $ docksh $ service apache2 start
在Firefox中输入about:preferences#privacy,在Authorities tab导入我们的CA并选择Trust this CA to identify web sites,最后访问https://www.example.com 即可
Task 5: Launching a Man-In-The-Middle Attack
中间人攻击通常发生在安全通信的建立阶段,例如使用SSL/TLS加密的HTTPS连接。攻击者会冒充服务器与客户端建立连接,同时与服务器和客户端分别建立独立的连接。攻击者可以生成自己的伪造证书,与客户端建立安全连接并将自己的伪造证书发送给客户端,同时与服务器建立另一个安全连接并将客户端的请求发送给服务器。这样,攻击者就能够在客户端和服务器之间的通信中拦截、查看和修改数据。
为了防止中间人攻击,通常使用证书颁发机构(CA)签发的可信证书来验证服务器的身份。客户端会对服务器的证书进行验证,包括验证证书的有效性、合法性和所属的颁发机构等。
几种方法可以让用户的 HTTPS 请求到达我们的 Web 服务器。
一种方法是攻击路由,这样用户的 HTTPS 请求就被路由到我们的 Web 服务器。
另一种方法是攻击 DNS,所以当受害者的机器试图找出目标网络服务器的 IP 地址,它得到我们的网络服务器的 IP 地址。
在这个任务中,我们模拟了攻击-DNS 的方法。我们只需修改受害者机器的/etc/hosts 文件,通过将主机名 www.example.com 映射到我们的恶意网络服务器,来模拟 DNS 缓存定位攻击的结果,而不是启动一个实际的 DNS 域名服务器缓存污染。
task4中,已经建立了一个 HTTPS 网站,这个任务中使用相同的 Apache 服务器来模拟 www.example.com 。方法类似按照 Task 4中的指令向 Apache 的 SSL 配置文件添加一个 VirtualHost 条目: ServerName 应该是 www.example.com
举个例子,可以将baidu.com映射到我们自己的服务器上,让受害者以为自己访问了百度,但是其实是访问了我们的恶意服务器
我们可以使用之前生成的自签名CA给百度签一个证书,如果浏览器加载了我们的CA,那么受害者访问百度的时候,就会显示https正常,通过了证书核验
Task 6: Launching a Man-In-The-Middle Attack with a Compromised CA
在这个任务中,我们假设在 Task 1中创建的根 CA 受到攻击者的攻击,并且它的私钥被盗取了。因此,攻击者可以使用此 CA 的私钥生成任意证书。在这项任务中,我们将看到这种妥协的后果。请设计一个实验来证明攻击者可以成功地在任何 HTTPS 网站上启动 MITM 攻击。您可以使用在 Task 5中创建的相同设置,但是这一次,您需要证明 MITM 攻击是成功的,也就是说,当受害者试图访问一个网站但是登录到 MITM 攻击者的假网站时,浏览器不会引起任何怀疑。
在task5中的叙述描述了我们使用自己的自签名CA导入到浏览器 的情况,但是如果根CA私钥 被盗取了会有更严重的后果:
伪造证书:攻击者可以使用根证书的私钥签发伪造的证书,模拟合法的网站或服务,使其看起来具有合法的身份和可信的安全性。这将导致用户误认为与真实网站或服务进行通信,从而暴露他们的敏感信息。
中间人攻击:通过拦截通信并使用伪造的证书,攻击者可以进行中间人攻击,监视和修改通信内容,窃取敏感信息或注入恶意内容。这对用户、网站和系统的安全性构成了严重威胁。
篡改和劫持:攻击者可以篡改通过伪造证书进行加密的通信内容,例如修改下载文件、注入恶意代码或劫持用户的会话。
信任破裂:如果根证书的私钥被盗取,信任链中的所有证书都将受到威胁,导致整个系统的信任破裂。这将对证书基础设施的安全性和可信度产生长期的负面影响。
实验步骤与之前类似,使用根CA签名证书,伪造证书在浏览器进行访问时不许任何设置都会被信任